Hello Everyone,
I am writing this blog to share screenshots for configuring certificate profiles with Intune.
Certificate profiles are used for authentication purpose which used trusted root certificate and helps user to access on-premises resources like email, WiFi and VPN profiles with secure process (using enterprise public key infrastructure). This helps users to configure devices automatically without any manual process or out of band process.
So, below are the prerequisites and steps by steps activities with screenshots. Hope this will help you in configuring :)
You can create 3 types of certificate profiles (PKCS #12 , SCEP and Trusted Root certificate profiles) and below are prerequisites for above certificate profiles:
Template Display Name:
On the Subject Name tab, select Supply in the request:
I am writing this blog to share screenshots for configuring certificate profiles with Intune.
Certificate profiles are used for authentication purpose which used trusted root certificate and helps user to access on-premises resources like email, WiFi and VPN profiles with secure process (using enterprise public key infrastructure). This helps users to configure devices automatically without any manual process or out of band process.
So, below are the prerequisites and steps by steps activities with screenshots. Hope this will help you in configuring :)
Management Capabilities:
- Android
- iOS
- Mac OS X
- Windows 8.1
- Windows Phone 8.1
Prerequisites:
You can create 3 types of certificate profiles (PKCS #12 , SCEP and Trusted Root certificate profiles) and below are prerequisites for above certificate profiles:
- Domain Controller
- Certificate Authority Server - Only Enterprise root CA server will work.
- NDES (Network Device Enrollment Service) Server - This can not be installed on CA server. The server on which it is configured must communicate with CA Server and also must have internet connectivity.
- NDES Service account - This must have enterprise admin rights and must be member of local Administrator and IIS_IUSRS group of NDES Server.
- Intune Certificate Connector - Download this connector from Intune administrator console (https://manage.microsoft.com)
Lets start with practical steps with screenshots:
STEP 1: Configure Certificate Authority:
-> Create Service account for NDES Server and make member of enterprise admin group:
-> Create Certificate Template with below configurations:
- On the Extension Tab, change Application Policies description to Client Authentication:
- On the Security Tab, Add the NDES Service account and give Read and Enroll permissions:
- Click Apply and OK:
-> Publish Certificate Template to Certificate Authority:
-> Verify if published template is visible in Certificate Template Folder:
STEP 2: Install prerequisites for NDES Server and Configure it:
-> You must login with NDES Service account.
-> Set spn for NDES service account:
-> Install ADCS Role on the server to Install NDES:
-> Select only Network Device Enrollment Service:
-> After installation, do not close window. Click on "Configure Active Directory Certificate Service on the destination server":
-> NDES Configuration windows will open, now follow steps as per below:
-> Select NDES Service account:
-> Close all windows now.
-> Open registry to edit for configuring certificate templates value with Certificate created in CA server: (Path: HLM\Software\Microsoft\Cryptography\MSCEP)
-> Restart IIS by command "iisreset":
-> Now, Install and Bind certificate on NDES Server by requesting a certificate with Server and Client Authentication from CA Server:
-> Open registry and add below DWORD value on path: "HLM\System\CurrentControlSet\Services\HTTP\Parameters" :
- MaxFieldLength - 65534
- MaxRequestBytes - 65534
STEP 3: Enable, Install and Configuring Intune Certificate Connector:
-> Open Intune Admin console (https://manage.microsoft.com) -> Go to Admin Tab -> Click on Certificate Connector and then Click on "Configure on-premises certificate connector":
-> Now, Download Intune Certificate connector by clicking on "Download Certificate Connector":
-> Install Certificate connector on NDES Server:
-> Click Sign-in:
-> Provide credentials in Advance Tab:
-> Click Apply and Close windows. Open Service console and restart "Intune Connector Service":
STEP 4: Configuring Certificate Profiles:
-> Export trusted root certificate from CA server which will be used in configuring trusted root certificate profile. (Using Trusted CA certificate profile, SCEP and PFX certificate profiles will be created which will be further used in EMAIL, WiFi and VPN Profile configurations):
-> Create Trusted CA Certificate profile:
-> Click Save Policy.
-> Create SCEP Profile:
-> Click Save Policy.
-> Create .PFX profile:
-> Click Save Policy. Now these profiles are ready for deployment. These can be deployed on user or device groups as well. All policies will be applied to applicable device platforms respectively.
NOTE: These above created profile policies are for Android Devices. Same can be configured for iOS, Mac OS X and Windows devices. (Note: PFX profiles is not available for iOS and Mac OS X as of now.)
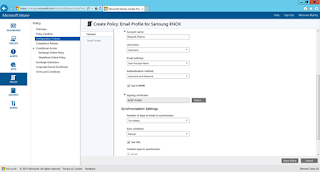
STEP 5: Creating E-mail Profile using above certificate profiles:
-> Create Email Profile policy:
-> Finally, All Profiles and policies are ready to deploy:
NOTE: Email Profiles for iOS and Windows are configured similarly(See steps for the same in below shared reference links). Also, same certificate profiles will be used for VPN and WiFi profiles.
Reference URLS:
- https://technet.microsoft.com/en-in/library/dn818904.aspx
- https://technet.microsoft.com/en-us/library/dn800672.aspx
- https://technet.microsoft.com/en-in/library/dn818903.aspx
- https://technet.microsoft.com/en-us/library/dn818905.aspx
- https://technet.microsoft.com/en-us/library/dn292747.aspx
Hope above steps helps you in configuration :).
I will share more posts in future and will keep updated...
For any query or suggestion, please feel free to post me back... If this helps anyone then I will feel appreciated!!!
Thanks in Advance for Your time to go through it!!!



















































The article posted was very informative and useful. You people are doing a great job. Keep going.
ReplyDeletecompany formation hong kong
Thanks Maria!!!
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteHi I am trying to configure the same on maas360. The steps seems to be similar. I didnt understand how to do this bit "Now, Install and Bind certificate on NDES Server by requesting a certificate with Server and Client Authentication from CA Server:" Could you please elaborate?
ReplyDeleteHey what a brilliant post I have come across and believe me I have been searching out for this similar kind of post for past a week and hardly came across this. Thank you very much and will look for more postings from you. hotmail sign in
ReplyDeleteIreland's optional schools are driven by a test arranged educational program. Branch of knowledge authorities show the entirety of the curricular substance. The backings accessible to kids with extraordinary needs are not broad or as tried as those at essential level. certificate iv in education support
ReplyDeletei never know the use of adobe shadow until i saw this post. thank you for this! this is very helpful. authority backlinks
ReplyDeleteThanks a lot...! I really admire to visit your amazing post and I wish to you different types of post.
ReplyDeleteTableau Training in Chennai
Tableau Course in Chennai
Advanced Excel Training in Chennai
Corporate Training in Chennai
Pega Training in Chennai
Linux Training in Chennai
Unix Training in Chennai
Oracle DBA Training in Chennai
Power BI Training in Chennai
Graphic Design Courses in Chennai
Tableau Training in T Nagar
On the off chance that you are dispatching a shiny new game vehicles or old fashioned vehicle, it's ideal to consider moving up to a higher premium to secure your venture. track china post to canada
ReplyDeleteI have seen some great stuff here. Worth bookmarking for revisiting. I surprise how much effort you put to create such a great informative website. Your work is truly appreciated around the clock and the globe. microsoft office 2016 product key
ReplyDeleteNice to be visiting your blog again, it has been months for me. Well this article that i've been waited for so long. I need this article to complete my assignment in the college, and it has same topic with your article. Thanks, great share. that
ReplyDeleteThanks for sharing this information with us.
ReplyDeleteyou can explore more-
quantitative vs qualitative
purple eyes
get out of facebook jail free card
should i buy iphone 6s
body temperature app
it companies
cyberflix apk
Excellent blog.thanks for sharing such a worthy information....
ReplyDeletebest digital marketing course in chennai
best digital marketing training in chennai
Happy to read the informative blog. Thanks for sharing
ReplyDeletepython coaching centre in chennai
python coaching centre in chennai
This post is so interactive and informative.keep update more information...
ReplyDeleteEthical Hacking Course in Velachery
Ethical Hacking Course in Chennai
Very informative & useful! Thank you for the post! https://bathroomremodelingeriepa.com/showers-tubs/
ReplyDeleteBest topic of this blog, technical skill enhancement is very important
ReplyDeleteamazing website... https://crackscoop.com
ReplyDeletei am visited this website daily.i liked it.i visit it daily.its stuff is very good.
ReplyDeleteI like this website. I am very satisfied with it.
ReplyDeletei like this website i will visit on daily basis for working useful thanks
ReplyDeletei like this website i will visitt on daily basis for working useful thanks
ReplyDeletegreat website .
ReplyDeletegreat website
ReplyDeleteGreat post! Class 8 is such an important year for building strong basics. I’ve noticed students do much better when they get support similar to 8th grade home tutors, especially through a reliable online tuition centre for class 8 where learning is more focused.
ReplyDelete